Wie SCIM mit Azure AD konfiguriert wird
Aktiviere Azure AD SAML für Single Sign-On in Zeeg mit unserer einfachen Anleitung zur Einrichtung von SSO mit Microsoft Entra-ID für verbesserten Benutzerzugriff und Sicherheit.
Zeeg ermöglicht eine nahtlose SCIM-Bereitstellung mit Azure Active Directory, die das Erstellen von Benutzern, Aktualisieren von Benutzerdetails wie Namen und E-Mails, Deaktivierung und Löschung ermöglicht. Diese Änderungen werden automatisch in Zeeg übernommen.
Anforderungen
Du musst eine Organisation in Zeeg haben.
Du musst Besitzer oder Administrator deiner Organisation sein.
Stelle sicher, dass die SAML Single Sign-On (SSO)-Einrichtung abgeschlossen ist, bevor du mit der SCIM-Konfiguration beginnst.
Während des Konfigurationsprozesses wird empfohlen, Zeeg und Azure-Plattformen gleichzeitig in verschiedenen Browserfenstern zu öffnen, um die Bedienung zu erleichtern.
Wenn SCIM aktiviert ist, können Benutzer deiner Zeeg-Organisation nur noch über Azure AD hinzugefügt/gelöscht werden und nicht mehr über Zeeg.
1. SCIM für deine Organisation in Zeeg aktivieren
Wähle in deinem Zeeg-Dashboard Deine Organisation aus.
Gehe zum SCIM-Reiter. (Dieser Reiter wird nur angezeigt, wenn du SSO aktiviert hast)
Klicke auf SCIM aktivieren; Zeeg wird dann ein SCIM Secret Token generieren und anzeigen, das in den nächsten Schritten verwendet wird.
2. SCIM-Bereitstellung in Azure AD einrichten
Öffne dein Azure-Portal in einem separaten Tab und navigiere zu Enterprise Applications > All applications.
Finde die Anwendung, die du für Zeeg erstellt hast, und klicke darauf.
Gehe in der linken Seitenleise zu Provisioning und wähle dann Get Started.
Wähle bei Provisioning Mode die Option Automatic.
Öffne den Admin Credentials Abschnitt in Azure:
Kopiere die Base URL aus deinem Zeeg SCIM-Dashboard und füge sie in das Feld Tenant URL ein.
Kopiere das SCIM Secret Token aus deinem Zeeg SCIM-Dashboard und füge es in das Feld Secret Token ein.
Klicke auf Test Connection. Du solltest eine Erfolgsmeldung von Azure erhalten.
Den Mappings-Abschnitt in Azure öffnen:
Zeeg unterstützt derzeit keine Gruppenbereitstellung; klicke daher auf Provision Azure Active Directory Groups. Stelle Enabled auf No. Dann Save und auf X klicken, um zur Mappings-Abschnitt zurückzukehren.
Klicke auf Provision Azure Active Directory Users. Wähle unter Target Object Actions Erstellen, Aktualisieren und Löschen.
Unter Attribute Mappings behalte die folgenden Azure-Attribute bei und lösche alles andere:
userPrincipalName
Switch([IsSoftDeleted], , "False", "True", "True", "False")
displayName
surname
country
mailNickname
Unter Attribute Mappings klicke auf jeden der folgenden Azure-Attribute und ändere das Source attribute entsprechend:
mail: ändere zu mail
mailNickname: ändere zu userPrincipalName
Das Endergebnis von Attribute Mappings sollte wie folgt aussehen:
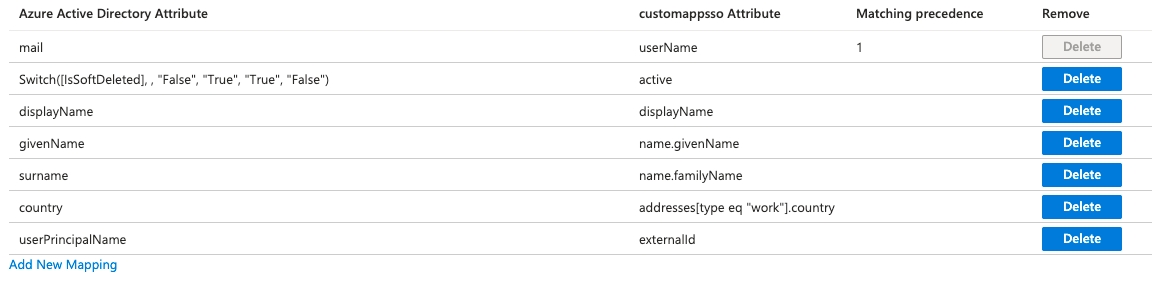
Klicke auf Save, dann Yes. Klicke schließlich auf das X oben rechts, um zur Hauptseite Provisioning zurückzukehren.
Öffne den Settings-Abschnitt in Azure.
Wenn du bei Synchronisierungsproblemen benachrichtigt werden möchtest, wähle "Send an email notification when a failure occurs" und gib eine E-Mail-Adresse ein.
Wähle bei Scope die Option Sync only assigned users and groups.
Stelle schließlich Provisioning Status auf On und klicke dann auf Save.
Beachte, dass die Bereitstellungssynchronisierung alle 40 Minuten erfolgt.
3. Benutzer der Zeeg Enterprise-Anwendung in Azure zuweisen
Wähle in Enterprise Applications in Azure die Anwendung aus, die du für SSO mit Zeeg erstellt hast.
Klicke unter "Getting Started" auf 1. Assign users and groups.
Klicke auf + Add user/group.
Unter Users, wenn du noch keine Benutzer zugewiesen hast, wirst du None selected sehen; klicke darauf.
Suche im geöffneten Feld nach Benutzern, wähle sie aus und klicke dann auf Select; das Feld wird geschlossen.
Klicke auf Assign.
Last updated